Amalgamated Security Services Limited utilizes the Cybersecurity Capability Maturity Model (C2M2) to conduct a comprehensive evaluation of deployed cybersecurity technologies, cybersecurity risk management policies, and processes utilized.
Amalgamated Security Services Limited utilizes the Cybersecurity Capability Maturity Model (C2M2) to conduct a comprehensive evaluation of deployed cybersecurity technologies, cybersecurity risk management policies, and processes utilized.
Cybersecurity is a critical aspect of a company’s technology infrastructure. Amalgamated Security Services Limited utilizes the Cybersecurity Capability Maturity Model (C2M2) to conduct a comprehensive evaluation of deployed cybersecurity technologies, cybersecurity risk management policies, and processes utilized. This cybersecurity capability analysis can then be used to create an actionable improvement plan with regular refreshes to deal with new threats and to track your cybersecurity capability over time, evolving your practices to better protect your business.
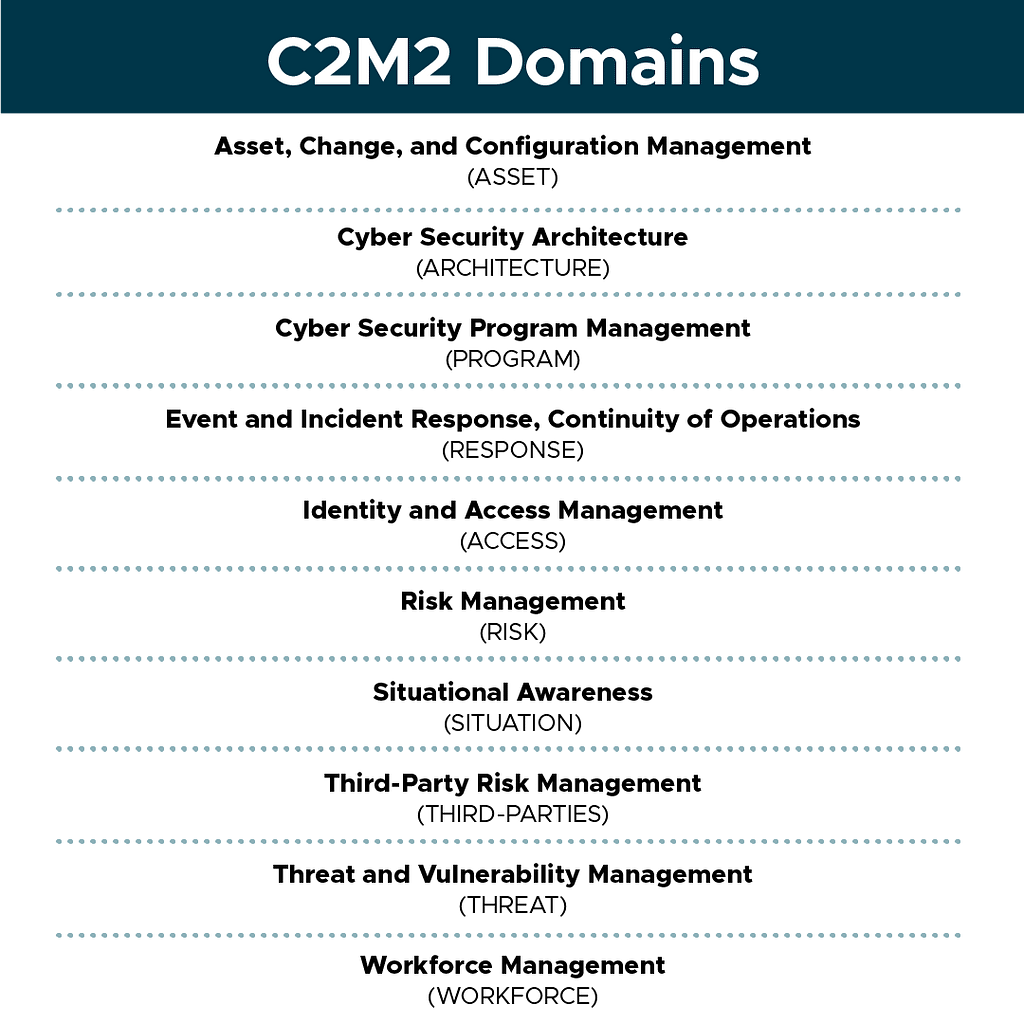
The C2M2 Model comprises domains, objectives, practices, and MILs (maturity indicator levels). Each component is discussed in the following sections.
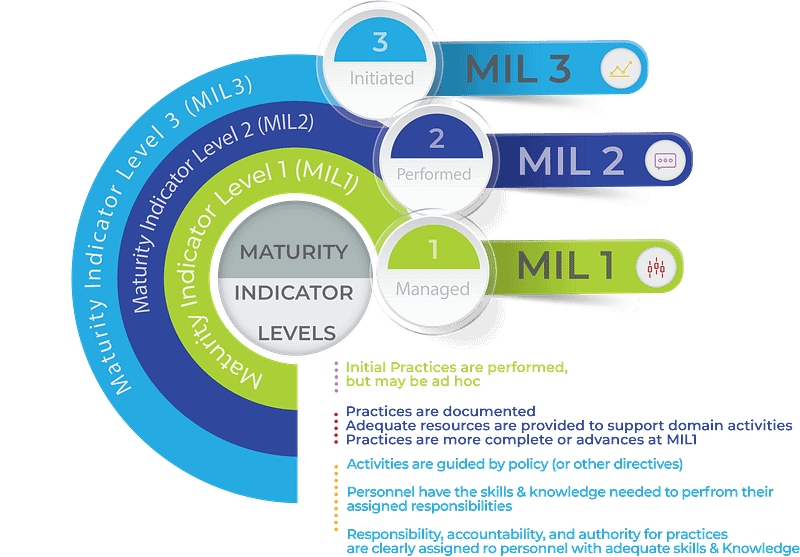
To measure progression, the C2M2 uses a 1-3 scale of maturity indicator levels. Each level represents maturity attributes, which are described in the table below. Organizations that implement the cybersecurity practices within each MIL achieve that level.
Having measurable transition states between the levels enables an organization to use the scale to define current and a more mature future state; and identify the capabilities it must attain to reach that future state.
Gather accurate data from your IT environment
Identify gaps in your cybersecurity capabilities
Prioritize recommended changes
Take action to create a more secure environment
Manage and measure your cybersecurity protection progress
References











Amalgamated Security Services Limited (ASSL) has been and remains the widely recognised leader in the expanding field of security and public safety services across Trinidad and Tobago, the Caribbean and internationally.
Mrs. Pamela Hosein
Email: phosein@assl.com
Tel: 626-2775
12 Garden Road, San Juan,
El Socorro 280711,
Trinidad and Tobago
© 2024 All Rights Reserved Amalgamated Security Services Ltd.
You cannot copy content of this page
Javascript not detected. Javascript required for this site to function. Please enable it in your browser settings and refresh this page.